SAML Authentication with Inline login¶
Usage scenario¶
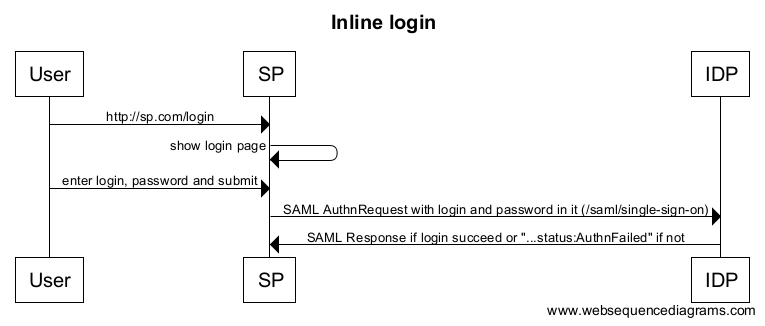
This extension to SAML Authentication creates a SAML SSO session in the SAML IDP. This SSO session is initiated by a SAML SP that presents its own login form to submit the credentials to the SAML IDP.
Flow¶
The SP should check whether the user has an SSO session with the SAML IDP using an Authentication Request with the IsPassive flag on true. This request should not contain the credentials of the user.
When the IdP returns the StatusCode urn:oasis:names:tc:SAML:2.0:status:NoPassive, the user is not logged in. The SP can now present a login form within its own UI.
When the user submits the login form, the SAML SP sends an Authentication Request to the SAML IDP. This Authentication Request must contain the credentials that were submitted by the user. The password must be encrypted. If the credentials are correct, the SAML IDP creates a session and proceeds with the login. If the credentials are incorrect, the SAML IDP must not present a login page, but returns a SAML response with feedback that authentication failed.
SAML Authentication Request¶
Example of an authentication request¶
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://sp/saml/SSO"
Destination="https://idp/saml/single-sign-on"
ForceAuthn="false"
ID="a33dd94jc826a5bc2f3754a1i62707i"
IsPassive="false"
IssueInstant="2016-02-09T12:40:57.727Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Version="2.0"
>
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">spring:security:saml</saml2:Issuer>
<saml2p:RequestedAuthnContext Comparison="exact">
<saml2:AuthnContextClassRef xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">
urn:onegini:names:SAML:2.0:ac:classes:InlineLogin
</saml2:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
<saml2p:Extensions>
<onegini:InlineLogin xmlns:onegini="urn:com:onegini:saml:InlineLogin"
IdpType="unp_idp">
<onegini:Credentials Username="foo@example.org"
Password="+V7wn+NyMG7cVelxIIiJYrUkqJiNDJRsqw=="
EncryptionParameter="+V7wNOIFDSYo8yhsfdhSAh9asdfDJRrqw=="/>
</onegini:InlineLogin>
</saml2p:Extensions>
</saml2p:AuthnRequest>
Authentication Context¶
The Authentication Context for inline login is urn:onegini:names:SAML:2.0:ac:classes:InlineLogin.
Inline Login SAML extension¶
The following XSD is defined for the SAML extension for inline login:
<xs:schema attributeFormDefault="unqualified"
elementFormDefault="qualified"
targetNamespace="urn:com:onegini:saml:InlineLogin"
xmlns:xs="http://www.w3.org/2001/XMLSchema">
<xs:element name="InlineLogin" type="urn:InlineLoginType"
xmlns:urn="urn:com:onegini:saml:InlineLogin"/>
<xs:complexType name="InlineLoginType">
<xs:sequence>
<xs:element type="urn:CredentialsType" name="Credentials" minOccurs="0"
xmlns:urn="urn:com:onegini:saml:InlineLogin"/>
</xs:sequence>
<xs:attribute type="xs:string" name="IdpType" use="required"/>
</xs:complexType>
<xs:complexType name="CredentialsType">
<xs:attribute type="xs:string" name="Username" use="required"/>
<xs:attribute type="xs:string" name="Password" use="required"/>
<xs:attribute type="xs:string" name="EncryptionParameter" use="required"/>
</xs:complexType>
</xs:schema>
IdpType: type of identity provider to log in into Onegini IdP. Currently onlyunp_idpis supported. The elementCredentialsis needed to authenticate with this identity provider.Username: the username of the user in Onegini IdP.Password: Base64 encoded, encrypted password of the user.EncryptionParameter: Base64 encoded encryption parameter that is used to encrypt the password.
The mechanism to encrypt the password is described in the documentation of the Password Encryption.
SAML Authentication Failure Responses¶
Onegini IdP returns the following StatusCodes for authentication failures that are specific for inline login:
- Incorrect credentials:
urn:oasis:names:tc:SAML:2.0:status:AuthnFailed
Example error response¶
<saml2p:Response xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
Destination="https://sp/saml/SSO"
ID="_3035bf33-f30b-4da6-9fb0-8f0bd7d76101"
IssueInstant="2016-02-18T15:20:37.718Z"
Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"
Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity">idp:saml
</saml2:Issuer>
<saml2p:Status>
<saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Responder">
<saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:AuthnFailed"/>
</saml2p:StatusCode>
<saml2p:StatusMessage>...</saml2p:StatusMessage>
</saml2p:Status>
</saml2p:Response>